shortstop20
Guest
- Messages
- 251
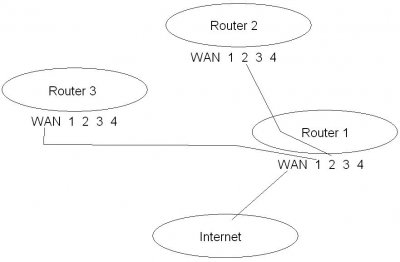
I currently have a home network setup at my home that has one WRT54G(connected to my DSL modem), and then a WRT54GL that is connected to the first router. This is all configured to be on the same network and works perfect, no problems there.
I am going to open my own computer repair business and would like to setup a network just for the repair business to keep the malware infected computers on a separate network from my personal machines. Here is a little diagram I drew up that shows how my network currently is setup. I don't want to purchase another phone line and internet connection because I know it's possible to prevent traffic from going to router 2 at all and only going to router 1 when router 3(and it's users want to access the net). Question is are the tools out there?
It's a pre-historic drawing at best, I know.
http://www.techist.com/forums/attachment.php?attachmentid=3139&stc=1&d=1229067938
I know plenty about networks but am a little concerned if when infected computers are connected to the office network to say, download spyware updates, etc. they may be trying to flood my home network with malware. A computer attached to router 3 could simply send a broadcast packet to discover responding hosts and then attempt to infect them.
Everything on Router 3(except the WAN IP Address) would be in a different network than the users connected to Routers 1 and 2 but that still doesn't stop the computers from broadcasting over the network in an attempt to discover hosts or plant malware on unprotected systems. Maybe I'm just paranoid or over protective but I was hoping there was a way I could prevent traffic coming from Router 3 from going anywhere except to Router 1 and out to the internet(for updates and such). I'm definitely not opposed to using some third party firmware, I've been thinking about it anyways. Something that would let me setup some "Cisco-like" ACL's would be PERFECT. Or is it possible that I can put one of the ports on router one in a DMZ. I've never used DMZ's much but that would put the port itself open to the internet and block any data coming from that port and going out the other ports correct?
Any opinions appreciated.
Well after I typed out that whole post and stared at the picture a little bit I had a revelation. Why not just attach router 3 directly to the internet and daisy chain routers 1 and 2 onto router 3. I can then set two different logical networks(168.32.16.0 /24 for Router 3 and 192.168.10 /24 for the network on Routers 1 and 2). Information from Router's 1 and 2 going to and from the Internet would have to pass through Router 3 but the information would not be broadcast through router three, it would be directed to the appropriate user on Router 1 or 2 via NAT/PAT translation. Any malicious information that a computer on Router 3 tried to pass onward to router one(and then maybe ultimately to router two) would be blocked by Router 1's WAN port(with the firewall active). Router 3's users could still connect to the internet fine though to download updates because they are connected directly to the DSL modem.
Am I missing something here or did I figure this out all by myself. LOL
Any help is appreciated guys.
I am going to open my own computer repair business and would like to setup a network just for the repair business to keep the malware infected computers on a separate network from my personal machines. Here is a little diagram I drew up that shows how my network currently is setup. I don't want to purchase another phone line and internet connection because I know it's possible to prevent traffic from going to router 2 at all and only going to router 1 when router 3(and it's users want to access the net). Question is are the tools out there?
It's a pre-historic drawing at best, I know.
http://www.techist.com/forums/attachment.php?attachmentid=3139&stc=1&d=1229067938
I know plenty about networks but am a little concerned if when infected computers are connected to the office network to say, download spyware updates, etc. they may be trying to flood my home network with malware. A computer attached to router 3 could simply send a broadcast packet to discover responding hosts and then attempt to infect them.
Everything on Router 3(except the WAN IP Address) would be in a different network than the users connected to Routers 1 and 2 but that still doesn't stop the computers from broadcasting over the network in an attempt to discover hosts or plant malware on unprotected systems. Maybe I'm just paranoid or over protective but I was hoping there was a way I could prevent traffic coming from Router 3 from going anywhere except to Router 1 and out to the internet(for updates and such). I'm definitely not opposed to using some third party firmware, I've been thinking about it anyways. Something that would let me setup some "Cisco-like" ACL's would be PERFECT. Or is it possible that I can put one of the ports on router one in a DMZ. I've never used DMZ's much but that would put the port itself open to the internet and block any data coming from that port and going out the other ports correct?
Any opinions appreciated.
Well after I typed out that whole post and stared at the picture a little bit I had a revelation. Why not just attach router 3 directly to the internet and daisy chain routers 1 and 2 onto router 3. I can then set two different logical networks(168.32.16.0 /24 for Router 3 and 192.168.10 /24 for the network on Routers 1 and 2). Information from Router's 1 and 2 going to and from the Internet would have to pass through Router 3 but the information would not be broadcast through router three, it would be directed to the appropriate user on Router 1 or 2 via NAT/PAT translation. Any malicious information that a computer on Router 3 tried to pass onward to router one(and then maybe ultimately to router two) would be blocked by Router 1's WAN port(with the firewall active). Router 3's users could still connect to the internet fine though to download updates because they are connected directly to the DSL modem.
Am I missing something here or did I figure this out all by myself. LOL
Any help is appreciated guys.