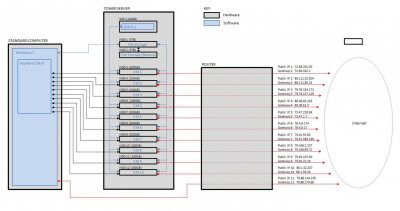
PP Mguire, my fundamental requirement is:
-That for each VM, the outside world should be able to read the public IP address, ISP and all the usual info that can be understood about a computer, but it would not link them to any of the other VM's on my server. (If when network discovery is turned off, it prevents the outside world reading the public IP address etc of each VM, then that might cause problems. This would be best left visible).
-They need to appear as separate unrelated computers/virtual machines - not seen to be linked by physical location or network.
I've taken all your suggestions into account and contacted a few Cisco Partners to see if they can provide me with the hardware and set everything up for me. I've had a few negative responses so far, here is one:
CISCO PARTNER:
"Dan,
Thanks for the update.
Sorry if I was misleading and I do appreciate your design. It is a completely
reasonable and normal set-up. The virtual servers will all be allocated a static
IP which is publicly routable and therefore will appear as though they are
separate.
Unfortunately it is very, very difficult to prevent someone knowing they are
on the same LAN. The reason is that you have one broadband connection and
router. For obvious reasons this means that you can physically have only one
actual presence on the internet (inside your ISP). If I were to perform a
trace route to each of the virtual servers then each listing would show the
IP address of the router connected to your broadband as the last hop. The IP
addresses of the VMs will all appear in the same range as well."
ME:
"Have you read the forum thread that I started? In this thread people who appear to be very knowledgeable about networking are suggesting that it would be possible to achieve this. If you have a few minutes, could you have a look at the thread? The main solution suggestions are on the 2nd page of the thread. Thanks.
CISCO PARTNER:
Dan,
I am a little swamped at present, but will try and review it in more detail
later. Of course there may be better placed people than I to answer this
question as I do not have that level of arrogance yet.
In overview, even if the ISP allocates you public IPs that are actually separate
networks the solutions still cannot work. Effort can be placed on achieving the
default route and network segregation of VMs, but to what avail. This is not
a significant challenge, but the fundamentals do change. You are using one
connection to your ISP and the outside interface of that router is going to be
assigned an IP by the ISP no matter what it is. All other IP's (traffic) will be
routed via this IP otherwise they will not get to you. Anyone worth their salt
will be able to determine that that the routed IPs are on the other side of
this IP.
I have refrained from asking what your intent is, because to large extent it is
irrelevant. However, it might help to understand this and suggest alternate
designs.
He seems to be suggesting it can't be done with 1 router - can anyone give an opinion on his thoughts? Thanks.
Dan